Save on cybersecurity upgrades
With this promotion, it’s never been simpler to upgrade your cybersecurity and enlist powerful SD-WAN technology.
Three clicks to secure SD-WAN.
Gain accuracy through a unique design that uses the same protocol for measuring path performance as real traffic.
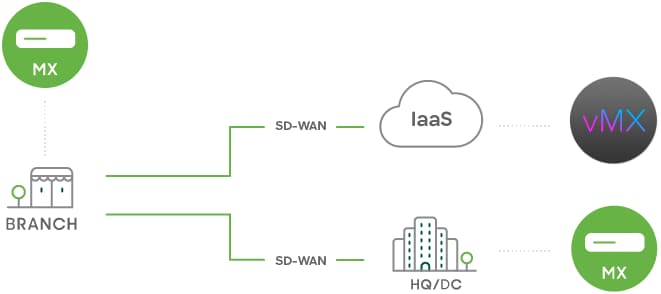
- Build resilient SD-WAN connectivity with integrated wired and cellular WAN, switching, and Wi-Fi
- Optimize traffic over all available paths, between sites and all multicloud environments—public and private
Complete cybersecurity protection. Simplified.
Automatically block 98% of malware—25% more than the industry average—with unmatched threat intelligence from Cisco Talos.
- Prevent real-time threats with a powerful, built-in, next-gen firewall including IDS/IPS, URL filtering, and malware protection
- Detect and respond to advanced threats automatically with Cisco XDR natively integrated
Proactively deliver exceptional experiences.
Transform the way you assure great end-user experiences and achieve digital resilience across any network.
ML-POWERED INSIGHTS
Get ahead of SaaS application issues
Identify issues as they happen with continuous monitoring across all internal and external domains.
ML-POWERED INSIGHTS
Get ahead of SaaS application issues
Identify issues as they happen with continuous monitoring across all internal and external domains.
Instant, always-on visibility for critical SaaS apps at scale.
Identify problems before users are impacted, whether apps are in use or not.
ML-powered corrective recommendations, including confidence ratings across LAN, WAN, and app servers.
Resource Hub
MX family datasheet
Learn more about the multifunctional network security and SD-WAN building blocks of a SASE architecture.
Learn moreIntroduction to Cisco Meraki Security and SD-WAN
Hear about the security and SD-WAN features of Meraki MX appliances and get a deep-dive demo.
Learn MoreCisco SD-WAN powered by Meraki overview
Get SD-WAN defined along with key use cases and a view of how SD-WAN powered by Meraki works.
Learn moreWhen to use on-premises or cloud security?
Discover the best practices for building a cloud-enabled network security model.
Learn moreNothing but the best for all your locations
Choose a best-fit mix of secure Cisco Meraki and Catalyst SD-WAN, and streamline management with a single dashboard.

Keeping 150+ locations secure and connected while reducing costs with SD-WAN.
- Cisco SD-WAN powered by Meraki provides branches with 20x more bandwidth and 4G backup
- 20% savings on WAN after replacing costly MPLS with broadband and fiber

Drove 40% cost savings across 42 financial services sites.
- Three network administrators oversaw wireless, switching, and secure SD-WAN
- Auto-provisioning secure SD-WAN fabric was key to savings in connectivity costs

Created significant cost savings through network upgrade to SD-WAN.
— Read Case StudyThe flexibility to work away from the office, if required, and access the dashboard from anywhere has been a great benefit. I would highly recommend Meraki.”
Chris Franks
Corporate Network Manager, ABHOW
A complete tool kit to build a complete experience.
Meraki security and SD-WAN appliances are uniquely designed to work with our teleworker and cellular gateways, wireless access points, switches, MDM, and IoT. Build experiences at scale with one platform.