A (Re)introduction to AI and IoT
Intros may not be necessary—you’ve likely already met. Artificial intelligence (AI) and the Internet of Things (IoT) are increasingly infused into our lives. In fact, the better these technologies work together, the less likely we are to think about how they interact. When things work, they just work (thanks, UX design!).
Yet those interactions are more potent than ever. Transforming data and connectivity through the network, AI and IoT are fueling one another’s rapid growth. Together, they can unlock tremendous efficiency and innovation, but to safely harness their potential, it’s important to understand what AI and IoT can offer to organizations—and to one another.
What is artificial intelligence?
Applications of AI are advancing so rapidly that only the latest breakthroughs tend to capture our attention. Today, when someone mentions AI, it’s easy to think “generative AI”—but AI still encompasses a broad array of computer science and engineering that simulates a human’s capacity to learn, perceive, reason, and problem-solve. Using AI technologies effectively requires a deeper understanding of the distinctions between different types.
AI can be as simple as reactive machines that perform a narrow range of tasks. These basic systems follow predefined rules and patterns, but don’t learn from historical data or adapt. Early chatbots, for example, might offer a limited selection of responses, and only if the user phrased their question a certain way.
Machine learning (ML) systems, on the other hand, learn from historical data and are designed to improve over time. Using advanced algorithms, ML applications are skilled at optimizing. ML-powered recommendation engines are a key feature driving modern consumer interactions with digital content. This has led to greater personalization of user experiences across e-commerce sites, streaming platforms, and workplace dashboards.
Deep learning is a characteristic of more advanced AI systems that use inference and neural networks to analyze complex data and develop sophisticated processing models. The emergence of large language models (LLMs) such as ChatGPT have shown deep learning’s transformative potential, enabling AI integration into diverse applications such as intelligent chatbots, financial trend analysis, and code debugging.
More sophisticated forms of AI often require more data. Large datasets help to ensure accurate parameters are set in complex models, contribute to a stable training process, and enable advanced AI to learn underlying patterns and capture nuanced features.
What is the Internet of Things?
The Internet of Things refers to a network of objects, such as devices, buildings, and vehicles. IoT connectivity is enabled by sensors, software, and technologies that allow these objects to collect and share data with one another using the internet. IoT sensors can also trigger transactions in response to the real-world data collected, such as climate or visual information. The process used to intercept and log traffic that passes over a digital network is referred to as packet capture. Data packets that are captured can then be analyzed to provide detailed insights and help diagnose network issues.
The decisions that an IoT system makes are determined in a control loop. Though similar to a reactive machine in the narrowness of its focus, an IoT control loop is a complex combination of hardware and software. Control loops leverage sensors, data processing units, actuators, and communication networks to manage things like temperature or lighting in complex environments. While not a form of AI, control loops can enable data-driven automation.
The potent intersection of AI and IoT
IoT technology is widely used to optimize energy usage, maintenance, and security in various settings. These include everything from smart factories and homes to traffic lights and hospitals. Different IoT devices and platforms communicate through application programming interfaces (APIs), which integrate data from multiple devices into centralized systems. APIs can also help manage the increased data load as more devices are added, allowing the network to scale efficiently.
There are several challenges in managing these interconnected devices, such as limited visibility for end users and complex network integrity. IoT devices generate massive amounts of data. While copious data is key for sophisticated AI models, it can become overwhelming to process—making network performance issues difficult to diagnose.
The network of devices also can become a vulnerable entry point for cyberattacks. As networks add complexity, attack surfaces proliferate. According to the 2024 State of Industrial Networking Report, mitigating against cyberthreats is the #1 challenge for companies running industrial infrastructure.
The combination of AI and IoT is helping to address some of the challenges in managing more complex networks. It’s also improving how devices interact and make decisions. Smart spaces and AI-enhanced data management systems are helping organizations digitally transform physical workspaces, gain control over environments, avoid costly disruptions, and protect individuals who access those spaces. Intelligent simulations are accelerating this transformation, compressing design cycles by applying AI algorithms to extract more insights from fewer simulations.
What are the benefits of combining AI and IoT?
AI helps to significantly simplify IoT network management and performance assurance. For instance, AI-driven channel planning uses advanced algorithms to monitor network conditions, tag severities, and avoid dynamic frequency selection (DFS) events that require frequency switching to prevent interference. AI can also help ensure compliance with local energy regulations by adapting transmission power based on range data and regulatory requirements.
AI also democratizes the power of IoT, allowing for more intuitive system interactions that use conversational prompts instead of highly technical queries. This allows administrators to quickly trigger packet captures, automate monitoring processes, and detect anomalies using preconfigured data from other deployments.
Used together, AI and IoT also enable simulations of environments to test virtual scenarios and optimize configurations. IoT systems can leverage the deep learning ability of AI to analyze vast amounts of data and predict outcomes, making those ecosystems and the components within them more adaptive and intelligent.
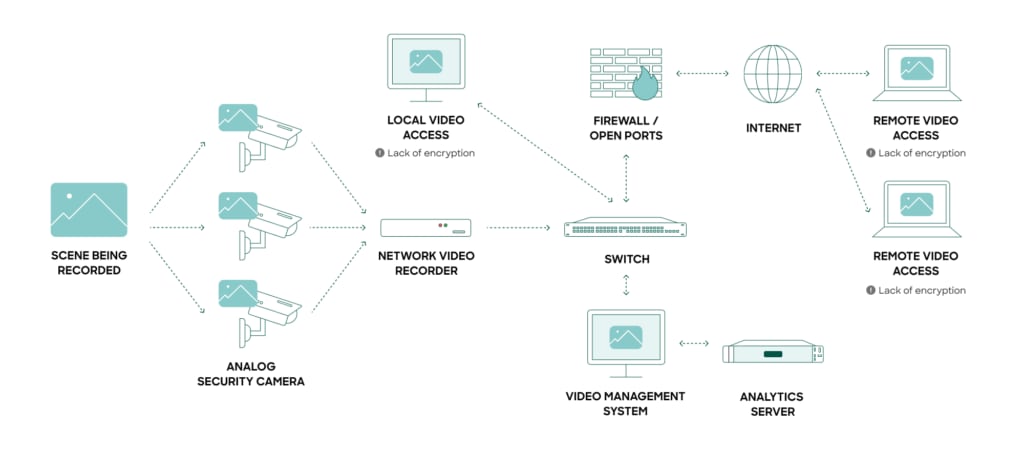
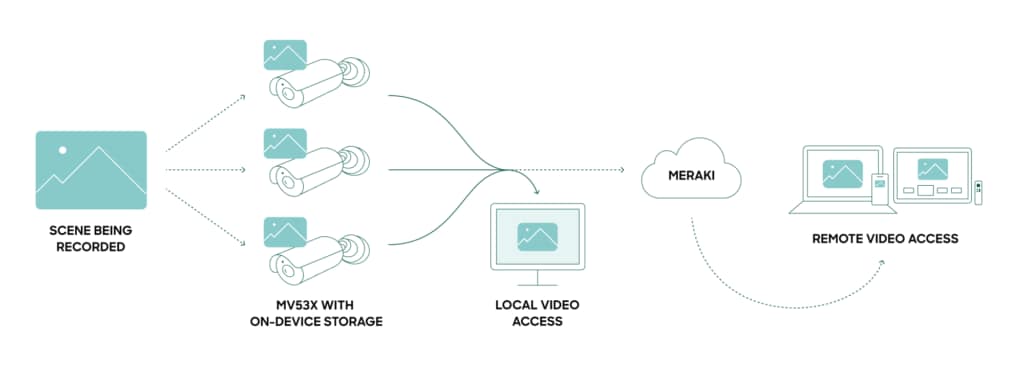
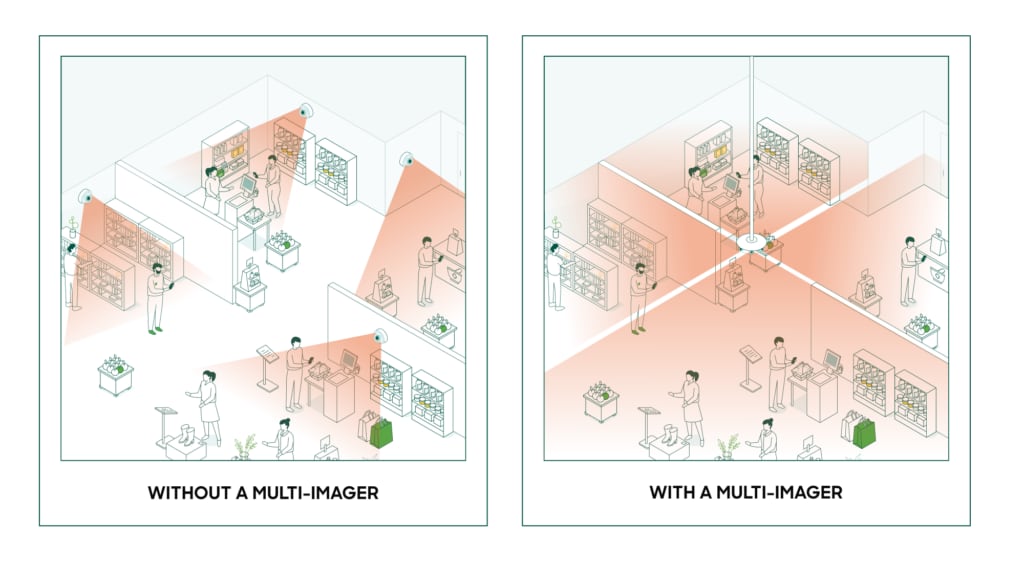
For example, smart cameras equipped with AI can analyze video feeds in real time, trained on models that allow them to detect and recognize anomalies, unusual activities, potential shortages, or even security threats. Surveillance systems that once required manual oversight and, in the case of incidents, laborious manual review of footage, are now transformed into proactive security solutions that can respond instantly. Triggers can even be set up to only activate threat response in anomalous conditions, such as when an RFID-tagged device leaves a designated area in a store.
The advanced analytics and machine learning capabilities of AI can be applied to data collected by these systems, offering nuanced insights that can improve interactions, refine resource allocation, and extend device life. Retailers can use AI and IoT cameras to track buyer sentiment through facial expressions and traffic patterns. Dwell time can be tracked using heat maps to inform improved equipment configurations and proper rotation.
The APIs that allow IoT devices to communicate with one another also facilitate custom AI solutions for IoT edge applications. AI that operates at the edge can be trained on highly relevant, real-time information, allowing it to quickly diagnose issues and pinpoint causes such as power outages, local environmental factors, connectivity problems, or user errors with a high accuracy and speed. By computing smart thresholds, AI reduces alert fatigue, providing more specific analysis and ensuring that resources are not wasted on misdiagnoses.
AI-enhanced radio resource management (RRM) can process and analyze 10 times the data of conventional methods—another boon for performance assurance. Optimizing radio configurations across multiple access points, RRM systems can help minimize or quickly resolve connectivity issues in complex wireless environments where any amount of latency can significantly impact the user experience.
Securing IoT and AI-based applications
Enhancing the security and performance of IoT networks with AI-based edge applications requires more agility and granular control over network traffic and device interactions than traditional virtual local area network (VLAN)-based approaches can offer. By dynamically adjusting security measures and resource allocation based on real-time data and contextual information, adaptive policy ensures that security protocols meet each device and application’s specific needs and behaviors.
By continuously monitoring network activity and device behavior, adaptive policies can identify anomalies and respond to threats with automatic segmentation and traffic isolation. Automating a segmented response minimizes the impact of security breaches and reduces the potential surface area for an attack.
Adaptive policies also help optimize resource allocation and performance by prioritizing critical applications, managing bandwidth efficiently, and dynamically adjusting to changing conditions and demands in the IoT ecosystem. This helps prevent bottlenecks and ensures that cameras, sensors, and other edge AI applications can function with low latency and high reliability.
Upcoming trends in AI and IoT development
What does the future of AI and IoT ecosystems look like? Less intrusive, for one thing. We’re already seeing the infrastructure efficiency in data centers being built to power AI computing. Informed by AI and IoT feedback and optimization, these new data centers require far less space than those of the past. As the use cases for smart and even autonomous IoT ecosystems abound, demand for elegant infrastructure could grow.
Whereas organizations once had separate systems to track people, inventory, and external threats, a platform environment is becoming more attainable than ever thanks to the integration of systems that AI and IoT are now making possible. As environments grow more personalized and complex, user controls should be simplified into a single dashboard experience that works so well you don’t even have to think about it.