Trust
Security, reliability & privacy information for Meraki cloud services
Overview

99.99% Reliability SLA

Highly Available Redundant Architecture

ISO 27001 Certified Data Centers (Non-US)

SSAE18 Type II Audited Data Centers (US)
Cisco Meraki operates the industry’s largest-scale cloud networking service. The Cisco Meraki cloud service powers millions of networks worldwide and connects hundreds of millions of devices every day. Cisco Meraki scales to fit the needs of businesses of every size, supporting networks with hundreds of thousands of devices at full enterprise scale, as well as small businesses with only a handful of users. Cisco Meraki also has extensive experience in the cloud, having run its cloud networking service continuously for more than 10 years. The Cisco Meraki cloud platform is trusted by thousands of IT professionals, from enterprises to hospitals, banks, and retailers.
The Cisco Meraki Trust Center website is a central repository of information regarding security, privacy, and reliability as related to Cisco Meraki cloud networking services. Here you will find information concerning:
- Our data centers, our security processes, and certifications
- How we safeguard your data
- Best practices for securing your organization’s network
- How Cisco Meraki networks continue to operate when disconnected from the cloud
- PCI compliance information, tools, and best practices
- Cisco Meraki’s Service Level Agreement
- Our data privacy practices and subprocessors
- Privacy sensitive feature information
Our Data Centers
The Cisco Meraki service is colocated in fully redundant, highly available data centers and select public cloud service providers (together, “data centers”). These facilities feature state of the art physical and cyber security, and maintain certifications such as PCI, SOC 2 and ISO 27001. All Cisco Meraki services are replicated across these multiple independent data centers, so that customer-facing services remain highly available in the event of a catastrophic data center failure.
Availability Monitoring
- 99.99% uptime service level agreement (that’s under one hour per year)
- 24×7 automated failure detection — all servers are tested every five minutes from multiple locations
- Rapid escalation procedures across multiple operations teams
- Independent outage alert system with 3x redundancy
Redundancy
- Globally distributed data centers
- Customer network configuration data and statistical data replicated across independent data centers with no common point of failure
- Real-time replication of data between data centers (within 60 seconds)
- Nightly archival backups for customer network configuration data and statistical data
Disaster Recovery
- Rapid failover to hot spare in event of hardware failure or natural disaster
- Out of band architecture preserves end-user network functionality, even if connectivity to the Cisco Meraki cloud services is interrupted
- Failover procedures drilled weekly
Cloud Services Security
- 24×7 automated intrusion detection
- Protected via IP and port-based firewalls
- Remote access restricted by IP address and verified by public key (RSA)
- Systems are not accessible via password access
- Administrators automatically alerted on configuration changes
Out-of-Band Architecture
- Only network configuration and usage statistics are stored in the cloud
- End user data does not traverse through the data center
- All sensitive data (e.g., passwords) stored in encrypted format
Physical Security
- A high security card key system and biometric readers are utilized to control facility access
- All entries, exits, and cabinets are monitored by video surveillance
- Security guards monitor all traffic into and out of the data centers 24×7, ensuring that entry processes are followed
Disaster Preparedness
- Data centers feature sophisticated sprinkler systems with interlocks to prevent accidental water discharge
- Diesel generators provide backup power in the event of power loss
- UPS systems condition power and ensure orderly shutdown in the event of a full power outage
- Each data center has service from at least two top-tier carriers
- Seismic bracing is provided for the raised floor, cabinets, and support systems
- In the event of a catastrophic data center failure, services fail over to another geographically separate data center
Environmental Controls
- Over-provisioned HVAC systems provide cooling and humidity control
- Flooring systems are dedicated for air distribution
Regular Vulnerability Scanning
- All Cisco Meraki data centers undergo daily vulnerability scanning by an independent third party
Data center Certification
- The Cisco Meraki service is collocated in fully redundant and highly available data centers
Storage Architecture
The Cisco Meraki Cloud Networking service is powered by a multi-tier data storage architecture. This architecture allows us to offer powerful capabilities such as the ability to upload and use custom floorplans, host custom splash pages, and provide in-depth Location Analytics as part of the dashboard and product experience. The Meraki storage architecture is designed to store different types of data in a highly redundant and scalable fashion.
There are three major types of data types stored by Cisco Meraki:
- Network configuration data – includes network settings and configurations made by customers in the Meraki Dashboard
- Network analytics data – client, traffic and location analytics data, providing visualizations and network insights into traffic and foot patterns across customer sites
- Customer uploaded assets – any uploaded assets including custom floorplans, splash logos and IVR menus / voicemail greetings
The above types of data are stored in different systems in order to optimize performance; for example, network analytics data is stored in a custom time-series database built by the Meraki team. Learn more
Although the three types of data above are stored in three unique systems, the goals and underlying principles of the various storage architectures are the same:
- Security – Using encryption and data segmentation, we ensure data is stored securely and effectively in a multi-tenant environment.
- Durability – Using versioning and replication, data can be accessed for long periods of time without sacrificing performance.
- Availability – For high availability, all types of data are continuously duplicated and stored on two separate Meraki cloud services, providing full redundancy in the event of a data center failure.
- Scalability – By building custom databases and building out our global data center footprint, we are constantly pushing the limit in terms of how much data can be stored and visualized.
By following these underlying principles, Meraki has created a best-in-class data storage architecture that allows for rapid data lookup, the ability for customers to upload custom assets, and highly redundant customer configuration backups.
User/Management Data Segregation

Cisco Meraki’s out of band control plane separates network management data from user data.
Network Management data
The data (e.g. configuration, statistics, monitoring, etc.) that flows from Meraki devices (e.g. wireless access points, switches and security appliances) to the Meraki cloud over a secure internet connection.
User data
Data related to user traffic (e.g. web browsing, internal applications). User data does not flow through the Meraki cloud, instead flowing directly to their destination on the LAN or across the WAN.
Advantages of an out of band control plane:
Scalability
- Unlimited throughput: no centralized controller bottlenecks
- Add devices or sites without MPLS tunnels
Reliability
- Redundant cloud service provides high availability
- Network functions even if management traffic is interrupted
Security
- No user traffic passes through Cisco Meraki’s data centers
- Enables HIPAA compliant network / PCI compliant
What happens if my network loses connectivity to the Cisco Meraki cloud?
With Cisco Meraki’s out of band architecture, most end users are not affected if Cisco Meraki hardware devices (e.g. wireless APs, switches or security & SD-WAN devices) cannot communicate with the Cisco Meraki cloud (e.g., because of a temporary WAN failure). In the event of such an interruption:
- Users can access the local network (printers, file shares, etc.)
- If WAN connectivity is available, users can access the Internet
- Network policies (firewall rules, QoS, etc.) continue to be enforced
- Users can authenticate via 802.1X/RADIUS
- Wireless users can roam between access points
- Users can initiate and renew DHCP leases
- Established VPN tunnels continue to operate
- Local configuration tools are available (e.g., device IP configuration)
While the Cisco Meraki cloud is unreachable, management, monitoring, and hosted services are temporarily unavailable:
- Configuration and diagnostic tools are unavailable
- Usage statistics are stored locally until the connection to the cloud is re-established, at which time they are pushed to the cloud
- Splash pages and related functionality will be unavailable
Security Tools
In addition to the Cisco Meraki secure out of band architecture and hardened data centers, Cisco Meraki offers a number of tools for administrators to maximize the security of their network deployments. Use of these tools provide optimal protection, visibility, and control over your Cisco Meraki network. This page contains information about how to quickly and easily increase the security of your meraki.com accounts and our recommended best practices for account control and auditing. For more information, see Cisco Meraki manuals.
Enable two-factor authentication
Two-factor authentication adds an extra layer of security to an organization’s network by requiring access to an administrator’s phone, in addition to her username and password, in order to log in to Cisco Meraki cloud services. Cisco Meraki’s two factor authentication implementation uses secure, convenient, and cost effective SMS technology: after entering their username and password, an administrator is sent an a one-time passcode via SMS, which they must enter before authentication is complete. In the event that a hacker guesses or learns an administrator’s password, she still will not be able to access the organization’s account, as the hacker does not have the administrator’s phone. Cisco Meraki includes two-factor authentication for all enterprise users at no additional cost.

Strengthen your password policies
You can configure organization-wide security policies for your Cisco Meraki accounts to better protect access to the Cisco Meraki dashboard. Under Organization > Configure, you may:
- Force periodic password change (e.g., every 90 days)
- Require minimum password length and complexity
- Lock users out after repeated failed login attempts
- Disallow password reuse
- Restrict logins by IP address

Enforce the principle of least privilege with role-based administration
Role-based administration lets you appoint administrators for specific subsets of your organization, and specify whether they have read-only access to reports and troubleshooting tools, administer managed guest access via Cisco Meraki’s Lobby Ambassador, or can make configuration changes to the network. Role-based administration reduces the chance of accidental or malicious misconfiguration, and restricts errors to isolated parts of the network.
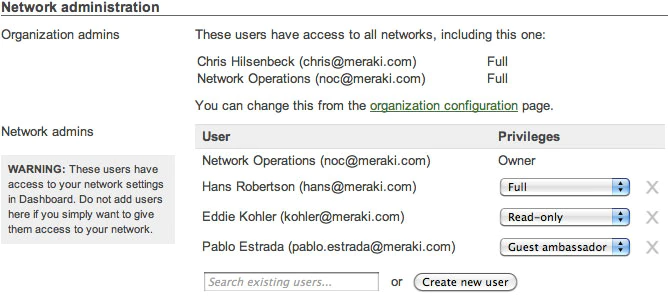
Enable configuration change email alerts
The Cisco Meraki system can automatically send human-readable email alerts when network configuration changes are made, enabling the entire IT organization to stay abreast of new policies. Change alerts are particularly important with large or distributed IT organizations.
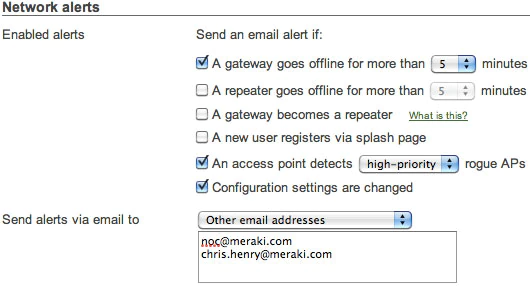
Periodically audit configuration and logins
Cisco Meraki logs the time, IP, and approximate location (city, state) of logged in administrators. Additionally, Cisco Meraki provides a searchable configuration change log, which indicates what configuration changes were made, who they were made by, and which part of the organization the change occurred in. Auditing configuration and login information provides greater visibility into your network.
Verify SSL certificates
Cisco Meraki accounts can only be accessed via https, ensuring that all communication between an administrator’s browser and Cisco Meraki cloud services is encrypted. As with any secure web service, do not log in if your browser displays certificate warnings, as it may indicate a man-in-the-middle attack.
Idle Timeout
30 seconds before being logged out, users are shown a notice that allows them to extend their session. Once time expires, users are asked to log in again.
PCI Compliance
Cisco Meraki provides a comprehensive solution to ensure a PCI compliant wireless environment held to the strict standards of a Level 1 PCI audit (the most rigorous audit level). Cisco Meraki’s rich security feature set addresses all of the PCI Data Security Standards, helping customers to build and maintain a secure network, protect cardholder data, maintain a vulnerability management program, implement strong access control measures, and monitor network security.
Unlike traditional networks, Cisco Meraki’s intelligent security infrastructure eliminates the management complexities, manual testing, and ongoing maintenance challenges that lead to vulnerabilities. Cisco Meraki’s intuitive and cost effective security features are ideal for network administrators, while powerful and fine-grained administration tools, account protections, audits, and change management appeal to CISOs.
Centrally managed from the cloud, Cisco Meraki makes it easy and cost effective to deploy, monitor, and verify PCI compliant networks across distributed networks of any size.
PCI-DSS requirements applicable to wireless LANs and their related Cisco Meraki features:
Cisco Meraki Infrastructure – Isolated from the Cardholder Data Environment
The Cisco Meraki cloud-hosted management system is out of band, meaning that traffic (including cardholder data) does not flow through Cisco Meraki’s cloud or any other Cisco Meraki infrastructure not behind your firewall. Learn more about Meraki’s out of band architecture.Cisco Meraki data centers are SSAE16 / SAS70 type II certified, feature robust physical and cyber security protection, and are regularly audited by third parties. Learn more about Cisco Meraki’s data centers.
Requirement 1.2.3 – Segregate Wireless Networks and the
Cardholder Data Environment
Cisco Meraki wireless APs include an integrated stateful firewall which ensures that guest WiFi users and other non-privileged clients cannot access cardholder data, in conformance with Requirement 1.2.3. The firewall’s LAN isolation feature enables one-click secure guest WiFi, wherein guests can only access the Internet. Blocked from LAN access, guests cannot spread viruses or reach internal resources. Cisco Meraki’s firewall provides fine-grained control, from layer 3 through 7. Configure VLAN tags, ACLs, identity-based policies, and block unwanted applications — even peer-to-peer apps without well-known hosts and ports.

Requirement 2.1.1 – Change Vendor Defaults and Enable Strong Encryption
Cisco Meraki does not ship with default vendor keys that need to be changed. Cisco Meraki hardware is configurable through an SSL-encrypted connection, accessible only by authenticated users. To comlpy with Requirement 2.1.1, simply enable strong security standards, such as WPA2 (802.11i). See Requirement 4.1.1 for more information on wireless encryption.
Requirement 4.1.1 – Encrypt Authentication and Transmission with
Industry Best Practices
Compliant networks require strong encryption using industry best-practices, e.g., WPA2, for wireless networks used for cardholder data. Cisco Meraki supports WPA2 (802.11i), offering both WPA2-PSK and WPA2-Enterprise with AES encryption. To maintain compliance with Requirements 4.1.1 and 2.1.1, enable WPA2 on any SSID that cardholder data is transferred over. Since Cisco Meraki’s firewall will isolate traffic between SSIDs, WPA2 need not be enabled on SSIDs that are not used for cardholder data (e.g. a guest WiFi SSID.)

Requirement 6.1 – Use the Latest Security Patches
Cisco Meraki firmware updates are delivered seamlessly from the cloud to APs, security appliances, and switches. When firmware updates are available, an administrator simply schedules an appropriate time for Cisco Meraki devices to download and install the new version, eliminating insecure and out of date firmware in the Cardholder Data Environment. This delivery model facilitates compliance with Requirement 6.1 – without deciphering compatibility matrices, time consuming manual updates, site visits to branch locations.

Requirement 7.2 – Restrict Access Based on a User’s Need to Know
Cisco Meraki provides role-based administration to enforce the principle of least privilege in compliance with Requirement 7.2. Role-based administration lets you appoint administrators for specific subsets of your organization and specify whether they have read-only access to reports and troubleshooting tools, can administer managed wireless guest access via Cisco Meraki’s Lobby Ambassador, or can make configuration changes to the network.

Requirement 8 – Implement User-Based Access Controls
Cisco Meraki includes a comprehensive suite of features to enable unique ID and authentication methods for network administration, in compliance with Requirement 8. Configure organization-wide security policies for your Cisco Meraki administrator accounts to better protect access to the Cisco Meraki dashboard and network infrastructure. These policies include account protections such as two-factor authentication, password hardening policies, and the use of encrypted transmission (SSL/TLS) for access to the Cisco Meraki dashboard.

Requirement 10 – Track and Monitor All Access to Network Resources
Cisco Meraki logs the time, IP, and approximate location (city, state) of logged in administrators. Additionally, Cisco Meraki provides a searchable configuration change log, which indicates what configuration changes were made, who they were made by, and which part of the organization the change occurred in. Auditing this configuration and access information satisfies Requirement 10 and provides greater visibility into your network.

Requirement 11.2/11.3 – Perform Regular Audits and Penetration Testing
Cisco Meraki data centers undergo thorough quarterly scans and daily penetration testing by Qualys, an Approved Scanning Vendor (ASV). Cisco Meraki is verified to be free of vulnerabilities such as injection flaws, cross-site scripting, misconfiguration, and insecure session management. Cisco Meraki data centers are SSAE16 / SAS70 type II certified and hardened against physical and network intrustion. These procedures exceed the scanning and penetration testing requirements of requirement 11.2 and 11.3, respectively.
Requirement 11.1/11.4 – Detect Unauthorized Access
Cisco Meraki’s out-of-the-box WIDS/WIPS, Air Marshal, protects the network from unauthorized wireless access points that may compromise network security. Rogue APs are unauthorized wireless APs that connect to your wired LAN, or that connect to a separate network but masquerade as part of your WLAN, using your same SSID. Cisco Meraki automatically detects rogue APs, identifying their IP address, VLAN, manufacturer, and model, and optionally contains them to neutralize their threat. Air Marshal includes network-wide visualization, email alerts, and reporting, meeting Requirements 11.1 and 11.4.

For more information about Cisco Meraki security capabilities, PCI compliance, and configuration best practices, please contact a Cisco Meraki specialist.
Privacy and Data Protection
Cisco Meraki is committed to data protection, privacy, security, and compliance with applicable regulatory frameworks in the US and abroad. The Meraki cloud-based architecture is designed from the ground up with data protection, privacy, and security in mind.
The Cisco Meraki technical architecture and its internal administrative and procedural safeguards assist customers with the design and deployment of cloud-based networking solutions. The cornerstone of Meraki’s privacy driven architecture is our out-of-band control plane. This means only network management information (not user traffic data) flows from devices to the Meraki cloud, dramatically limiting the amount of personal data that is transferred to the Meraki cloud. For more information on how Meraki products separate network management data from user data, see here.
In addition:
- Cisco Master Data Protection Agreement (MDPA)—The Cisco MDPA reflects our commitment to privacy, data security, and accountability for our customers, worldwide. For more information regarding how we protect your personal data, Cisco’s overall approach to data protection and privacy, and to view the MDPA, please see here. If you would like to put in place the MDPA, please contact your Cisco Meraki account representative to get started.
- Privacy Data Sheet—The Cisco Meraki Privacy Data Sheet, which details the privacy features and functionality of the Meraki products, is available here.
- GDPR—The European Union General Data Protection Regulation (GDPR) brings consistency to the data protection landscape in Europe. GDPR embodies the well-recognized privacy principles of transparency, fairness, and accountability. Cisco Meraki is committed to helping our customers and partners by protecting and respecting personal data, no matter where it comes from or where it flows. The MDPA described above incorporates the most current Standard Contractual Clauses adopted by the European Commission (also known as the EU Model Clauses) so that customers may allow transfer and processing of personal data outside the EEA in accordance with applicable European privacy and data protection regulations and local laws, including the GDPR. Read more here.
Subprocessors
At Meraki, we are committed to providing our customers with secure and intuitive product experiences. From time to time, we partner with third party service providers who are contracted to provide the same level of data protection and information security that customers expect from Meraki. Some of these third parties are engaged as “subprocessors” to process customer data, including limited personal data, in connection with providing Meraki products, including dashboard.
A current list of subprocessors is set out below. Meraki may update this list from time to time.
Hong Kong
Ireland
Japan
Netherlands
Singapore
United States
Singapore
United States
United Kingdom
This page is provided for informational purposes only.
Service Level Agreement
Cisco Meraki Cloud-Networking
This Service Level Agreement (“SLA”) applies to the Cisco Meraki Cloud Services as set out in the Offer Description. If capitalized terms are not defined in this SLA, then they have the same meaning as under the Offer Description.
1. Service Level
Cisco will use commercially reasonable efforts to deliver the Cloud Service so that the Core Services meet or exceed the performance standards described below (“Service Level”). Subject to the terms of this SLA, You are eligible for Service Credits if Cisco fails to meet the Service Level.
2. Service Credits
2.1 Service Credits. If Cisco fails to meet the Service Level for a given Measurement Period, Cisco will issue You a Service Credit consistent with the table below.
2.2 Service Credit Limitations
The aggregate maximum Service Credit for any Measurement Period will be 15 days of additional Cloud Service for that Measurement Period.
These Service Credits are Your only remedy if the Core Services do not meet the Service Level.
3. Claims Procedure
3.1 To receive a Service Credit, You must:
(A) be up to date on payment of all applicable fees;
(B) promptly notify Cisco of a Qualifying Outage when You become aware of or reasonably suspect one; and
(C) request Service Credits no more than 30 days after the end of the applicable Measurement Period.
3.2 You must submit a claim via Meraki Support.
3.3 If You purchased the Cloud Service from a Cisco Partner, You may claim Service Credits or the Cisco Partner may claim them on Your behalf.
3.4 If there is a dispute about whether a Qualifying Outage has occurred, Cisco will decide in good faith based on our system logs, monitoring reports, and configuration records. If You have supporting information for Your claim that You want Cisco to consider, You should provide this information with Your claim.
4. Issuance
4.1 Review. Cisco will use commercially reasonable efforts to review and issue earned Service Credits within 30 calendar days of confirming that You are entitled to those Service Credits.
4.2 Service Credits.Service Credits that Cisco issues will be added to the end of Your existing Usage Term. You will be responsible for arranging adjustments to the term for any other Cisco Offers or Services that depend on the Cloud Service (which may have a fee). You cannot convert Service Credits to general credits or refunds, and You cannot sell, transfer, or assign such Service Credits. Cisco will use commercially reasonable efforts to notify the Cisco Partner of the awarded Service Credits.
5. Non-Qualifying Outages
It is not a Qualifying Outage and You will not be eligible for Service Credits if Cisco fails to meet the Service Level for any of the following reasons:
(A) Scheduled maintenance or emergency maintenance (‘emergency maintenance’ is unscheduled maintenance where Cisco performs work to prevent or mitigate an outage or degradation of the Cloud Service or to prevent or mitigate a security incident);
(B) Due to Your integrations or any applicable third-party software, hardware, or services not provided by Cisco;
(C) You are using a beta, evaluation, or trial version of the Cloud Service;
(D) Your failure to (1) use the Cloud Service or perform responsibilities in accordance with Your applicable agreement (e.g., EULA or General Terms), Offer Description, Enterprise Agreement, or the Documentation, or (2) apply updates or upgrades when made available; or
(E) Factors outside of our reasonable control, such as events described as Force Majeure in Your applicable agreement, Internet outages, pandemics, acts of government, industry-wide shortages, failures, or delays of common carriers.
6. Definitions
Total Service Time – Total Outage Time
Total Service Time
The aggregate total time for all Qualifying Outages during a Measurement Period (rounded upward to the nearest minute). To calculate Total Outage Time, each Qualifying Outage will:
(A) Begin when Cisco logs an incident ticket based on our own identification of a Qualifying Outage or upon confirming a Qualifying Outage You report to Cisco; and
(B) End when the Core Services are restored.
Translated Service Level Agreement
Cisco Meraki provides certain translated versions of the Service Level Agreement at the link(s) below.
To view the Service Level Agreement in French (Canada), please click here.
Vulnerability Reporting & Rewards
The security of our customers and end users are our top priority. We invest heavily in tools, processes, and technologies to keep our users and their networks safe. This includes third-party audits, threat modeling, penetration testing, features like two-factor authentication, and our out-of-band cloud management architecture. The Cisco Meraki Vulnerability Reporting Program is a crucial element of our comprehensive security strategy, promoting active collaboration among our customers, external researchers, and the public with a shared goal of enhancing the safety and security of our customers.
If you are a user and have a security issue to report regarding your account (including password problems and account abuse issues), non-security bugs, or questions about issues with your network, please contact Cisco Meraki Support.
Reporting Security Issues
If you think you’ve discovered a vulnerability in a Cisco Meraki product or service, please report it through our Vulnerability Reporting Form below. We welcome all relevant reports to help us improve our security posture. Additional information on this program, including our commitment and details about disclosure are available on our Bugcrowd Responsible Disclosure Program Landing Page.
Security Rewards Program
To participate in our Security Rewards Bug Bounty Program, which provides monetary rewards for verified vulnerabilities, please visit our Bug Bounty Program through Bugcrowd. The program has specific limitations regarding scope and vulnerability types; therefore, we encourage you to thoroughly review the detailed targets that are in and out of scope, the rewards offered, and the guidelines on permissible activities.
Reporting Cisco (Non-Meraki) Security Issues
Please note that this program does not cover vulnerabilities related to other parts of Cisco Systems, Inc.
- To report a vulnerability in Cisco Systems operational infrastructure, visit the Cisco Responsible Disclosure page.
- To report a vulnerability in a Cisco (non-Meraki) product, please contact
psirt@cisco.com. - To report a security incident to Cisco, please contact incidentresponse@cisco.com.
Vulnerability Reporting Form
Location Analytics
Overview
Cisco Meraki’s cloud-based location analytics and user engagement solution provides data about the physical locations of visitors, enabling businesses to better understand the behavior of clients. Location Analytics is available with all Cisco Meraki wireless access points.
Location Analytics data is gathered by capturing and analyzing the beacons that every Wi-Fi enabled device periodically emits when its Wi-Fi antenna is turned on in order to detect the presence of nearby wireless networks. The Cisco Meraki dashboard also displays anonymized and aggregated statistics on nearby devices, whether they join the network or not.
Location Analytics distinguishes between devices and recognizes repeat visitors by collecting a MAC address, the unique identifier assigned to every device connecting to wired or wireless networks. Only a device’s MAC address is captured, and the aggregated data provided to businesses using Location Analytics can’t be traced back to an individual without the business having prior knowledge of the MAC address of that person’s device.
You can learn more in our documentation on Location Analytics.
Storing Data
Cisco Meraki uses a one-way hash function to anonymize MAC addresses before storage. The function is irreversible; given a specific hashed MAC, there is no way to undo the function to reveal the original MAC address. In addition, bytes are dropped from the hashcode, meaning that even if one knew the hash function, they could not determine if a specific MAC had visited a location. Hashed MAC addresses are unique to each business or organization, so it is not possible to view Location Analytics data for a single device across networks with different owners.
Our data centers are protected by enterprise-class physical and network security, and are subjected to regular audits and penetration tests by independent third parties.
Location Analytics API
In addition to providing statistics to businesses within the Cisco Meraki dashboard, customers can use the Location Analytics API to export MAC addresses of probing clients, consistent with industry standards. Retail and enterprise customers can use the Location Analytics API to integrate Location Analytics data from their network with their own custom-built applications.
The Location Analytics API provides no mechanism for users to connect MAC addresses with any other personal information.
We provide a set of best practices to users of the Location Analytics API, and it is their responsibility to take appropriate measures to safeguard the privacy of personally identifiable information that they may collect.
Opt Out
If you would like to exclude your Wi-Fi-enabled devices from Meraki Location Analytics services, you may do so through a simple opt-out form, available here https://account.meraki.com/optout.Opting out will exclude your MAC address from Location Analytics information stored in the Cisco Meraki cloud and from export through the Location Analytics API. It is the Cisco Meraki customer’s responsibility to notify visitors to their network that Location Analytics services are in use.
Technical and Organizational Measures
Introduction
Meraki takes a systematic approach to data protection, privacy, and security. We believe a robust security and privacy program requires active involvement of stakeholders, ongoing education, internal and external assessments, and instillment of best practices within the organization.
Physical Access and Admittance Control
To deny unauthorized persons access to data processing systems in which Customer Data is processed.
This is accomplished by:
- Secure account credentials including two-factor authentication.
- Account security protections (strong passwords, maximum number of failed attempts, IP based login restrictions, etc.)
- Change management including change logs and change event alerting.
- 24×7 automated intrusion detection.
- A high security card key system and biometric readers are utilized to control facility access.
- All entries, exits, and cabinets are monitored by video surveillance.
- Security guards monitor all traffic into and out of the data centers 24×7, ensuring that entry processes are followed.
- Software development life cycle and change management / change control policy and processes.
- Product development secure coding guidelines and training policy and procedures.
- Access to Customer data restricted to personnel based on appropriate business need and limited by functional role.
Access Control
To prevent data processing systems from being used without authorization.
This is accomplished by:
- Software development life cycle and change management / change control policy and processes.
- Access to Customer Data restricted to personnel based on appropriate business need and limited by functional role.
- Information security responsibilities for employees.
- Audit trails policy and procedures, and history and log retention policy and procedures.
- Data control and access control policies and procedures.
Data Access Control
To ensure that persons authorized to use systems in which Customer Data is processed only have access to the Customer Data as they are entitled to in accordance with their access rights and authorizations, and to prevent the unauthorized reading, copying, modification or deletion of Customer Data.
This is accomplished by:
- Access to Customer Data restricted to personnel based on appropriate business need and limited by functional role.
- Audit trails policy and procedures, and history and log retention policy and procedures.
Data Transfer Control
To prevent the unauthorized reading, copying, modification or deletion of Customer Data which is under Meraki’s control while Customer Data is being transferred electronically, transported or recorded on data storage devices, and to ensure that the intended recipients of Customer Data who are provided with Customer Data by means of data communication equipment can be established and verified.
This is accomplished by:
- Encrypted communication between Meraki hardware devices and Meraki’s servers (HTTPS / SSL), as well as between Meraki’s servers.
- Logging of activity of administrators (time, IP, and approximate location (city, state) of logged in administrators).
- Account passwords stored in encrypted format on Meraki servers.
- Full disk encryption on all Meraki servers
Input Control
To ensure it is possible to establish an audit trail as to when and by whom Customer Data has been entered, modified, or removed from systems being used by (or on behalf of) Meraki to process Customer Data.
This is accomplished by:
- Logging of activity of administrators (time, IP, and approximate location (city, state) of logged in administrators).
- Access to Customer data restricted to personnel based on appropriate business need and limited by functional role.
- Data control and access control policies and procedures.
- Customer’s ability to block entirely Meraki’s access to Customer’s Hosted Software account and prevent Meraki from accessing Customer Data.
- Session timeouts.
Order/Instruction Control
To ensure that Customer Data processed by or on behalf of Meraki can only be processed in accordance with the Customer’s instructions.
This is accomplished by:
- Change management including change logs and change event alerting.
- Audit trails policy and procedures, and history and log retention policy and procedures.
- Customer can entirely block Meraki’s access to Customer’s Hosted Software account thereby preventing Meraki from accessing Customer Data.
Availability Control
To ensure the protection of Customer Data which is under the control of Meraki against accidental destruction or loss.
This is accomplished by:
- 99.99% uptime service level agreement.
- Customer network configuration data and statistical data replicated across independent data centers with no common point of failure.
- Real-time replication of data between data centers (within 60 seconds).
- Nightly archival backups for customer configuration data and statistical data.
- 24×7 independent outage alert system with 3x redundancy.
Intended Use Control
To ensure that Customer Data collected is only used for the intended purpose under the Agreement.
This is accomplished by:
- Customer Data used exclusively to provide the features and functionality available in the hosted software.
- Customer Data is automatically processed according to the specific features enabled by the customer and as required to secure and maintain the infrastructure.
- Change management including change logs and change event alerting.
- Audit trails policy and procedures, and history and log retention policy and procedures.
- Customer can entirely block Meraki’s access to Customer’s Hosted Software account thereby preventing Meraki from accessing Customer Data.
Documentation
Meraki keeps documentation of organizational and technical measures in case of audits. Meraki takes reasonable steps to ensure that its employees and other persons at Meraki physical locations are aware of and comply with the organizational and technical measures set forth in this document.
Additional Measures
Out-of-Band Architecture
- Only network configuration and usage statistics are stored in the cloud.
- Data stored or transmitted by means of Customer’s network does not traverse Meraki’s servers.
Cloud Services Security
- Daily vulnerability testing of data center infrastructure.
- Protected via IP and port-based firewalls.
- Remote access restricted by IP address and verified by public key (RSA).
- Systems are not accessible via password access.
- Administrators automatically alerted on configuration changes.
Cloud Services Infrastructure
- Data centers are certified by industry-recognized standards such as ISO 9001:2008, ISO 27001, PCI DSS, SSAE16, and ISAE 3402 (SAS70) including Type II.
- Configuration standards for all system components policy and procedures.
- 24×7 automated failure detection — all servers are tested every five minutes from multiple locations.
- Systems are not accessible via password access.
- Administrators automatically alerted on configuration changes.
Disaster Preparedness
- Data centers feature sophisticated sprinkler systems with interlocks to prevent accidental water discharge.
- Diesel generators provide backup power in the event of power loss.
- UPS systems condition power and ensure orderly shutdown in the event of a full power outage.
- Seismic bracing is provided for the raised floor, cabinets, and support systems.
- In the event of a catastrophic data center failure, services failover to another geographically separate data center.
Organization and Personnel
- Formal assignment of information security responsibilities by the Security Director and the Meraki Security Team.
- A formal security awareness program.
- Documentation and business justification for use of all services, protocols and ports allowed.
- Management of service providers policy and procedures.
- Criminal background review of all Meraki personnel.
- Administrators automatically alerted on configuration changes.
- Rapid escalation procedures across multiple operations teams.
Cloud Service Communication
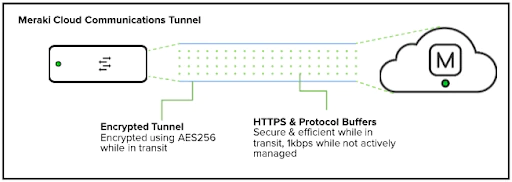
Device-to-Cloud – Meraki Cloud Communications Tunnel
For a Meraki hardware device to communicate with the cloud, Meraki leverages a lightweight encrypted tunnel using AES256 encryption while management data is in transit. Within the tunnel itself, Meraki leverages HTTPS and Protocol Buffers for a secure and efficient solution, limited to 1 kbps per device when the device is not being actively managed.
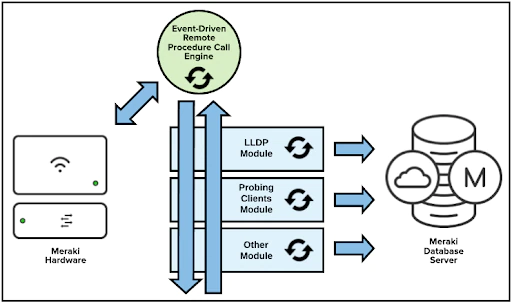
Cloud Communications Process
Meraki uses an event-driven Remote Procedure Call (RPC) engine for Meraki devices to communicate to the Meraki dashboard and for Meraki servers to send and receive data. Meraki hardware devices act as the server/receiver as the Meraki cloud initiates calls to the devices for data collection and configuration deployment. Because the cloud infrastructure is the initiator, configurations can be executed in the cloud before the devices are actually online, or even physically deployed.
In the event of cloud connectivity loss (which is most commonly caused by a local ISP or connection failure), the Meraki hardware device will continue to run with its last known configuration until cloud connectivity is restored.
Device-to-Device – Meraki Auto VPN
Auto VPN is a proprietary technology developed by Meraki that allows you to quickly and easily build VPN tunnels between Meraki MX devices at your separate network branches with just a few clicks. Auto VPN performs the work normally required for manual VPN configurations with a simple cloud based process.
Meraki MR access points may also be configured to concentrate traffic to a single point either for layer 3 roaming or teleworker use cases. SSID tunneling and Layer 3 roaming with a concentrator both use the same Meraki Auto VPN technology. Wireless access points should concentrate to a Meraki MX security appliance.
How Meraki Auto VPN Works
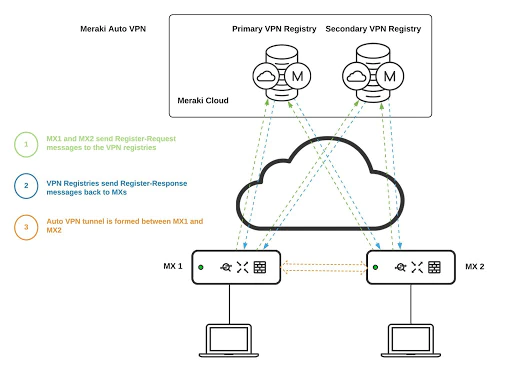
- VPN Registry: This is the main server mechanism that allows Auto VPN to happen. It is a cloud service that is used to keep track of the contact information for all the MX devices participating in Auto VPN for an organization.
- Hub: Hubs are MX devices in a VPN topology that service connectivity from a remote peer site (such as a spoke) to the hub and the hub to the remote peer site. Hubs also act as a gateway for remote peer sites to communicate with each other via the hub.
- Peer: This refers to another MX or MR within the same organization that a local MX will form or has formed a VPN tunnel to. This could be an MX or an MR in the case of SSID tunneling or layer 3 roaming with a concentrator.
- Contact:This is the public IP and the UDP port that the MX will communicate on for Auto VPN.