When it comes to hybrid work, there are many network security implications to consider. As IT teams build more distributed, flexible networks, the challenge of identifying persistent threats and detecting unwanted network activity in encrypted traffic increases.
The necessity for remote work has accelerated investment in more flexible, collaborative operations. At the same time, the need to protect customer and corporate data as it travels is accelerating the adoption of encryption across the enterprise. Without some advanced planning, these two positive trends can combine to create a new challenge for network and security teams.
Distributed blind spots
To put this into perspective, we’ve seen the average number of sites managed on a Meraki network blossom over the past two years as companies adapt to a more distributed workforce. A 2021 Ponemon report observed that over the same period, the percentage of organizations that have established enterprise-wide data encryption plans has rapidly exceeded 87%.
The potential risk? Network traffic blind spots for security teams. The demand for smarter, more connected, more flexible workspaces increases the amount of encrypted internal traffic on the network, creating significant opportunities for attackers to hide in plain sight.
Device telemetry for threat analysis
Fortunately, there is an approach that can address these risks using your existing network infrastructure that provides full visibility into who is acting on your network and how—and it doesn’t require additional costly sensors or a slowing of traffic for inspection.
The Meraki MS390 can provide rich, detailed telemetry about application and endpoint behavior for every device on a Meraki network. By pairing this data with Cisco’s Secure Network Analytics, you can perform encrypted traffic analytics (ETA) to detect malware and govern the quality of the network across your business.
Creating a security baseline
Secure network analytics closely monitors the activity of every device on the network and can create a baseline of normal behavior for your organization. From there, it applies advanced behavioral modeling, layered machine learning, and global threat intelligence from Cisco Talos and its group of security experts to build a sense of what’s normal, what’s anomalous, and what qualifies as threat activity on the network.
By taking this approach, you can proactively identify threats hiding in encrypted traffic without increasing your investment in add-on sensors or expensive in-line traffic decryption, all without compromising the confidentiality or integrity of customer and employee data.
Detecting threats made simple
Customers have used this technique to uncover malware hidden in encrypted traffic, detect activities associated with advanced persistent threats, and even identify illicit cryptocurrency mining services running within the network. Based on the Cisco Hybrid Work Index, these are some of the top queries blocked by Umbrella through the end of last year.
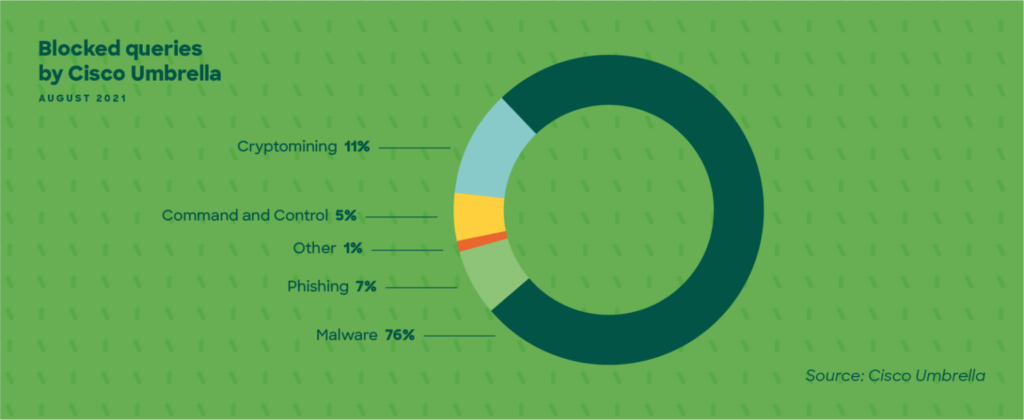
We’ve recently enabled encrypted traffic analytics for the Meraki MS390 with the firmware 15 beta release. To get started using your Meraki network as a security sensor, update your switches to firmware 15 via the dashboard. Or, request a demo today if you’d like to see Meraki and secure network analytics in action.