We recently introduced two-factor authentication for Meraki dashboard accounts. Administrators can add an extra layer of account security to their networks by requiring more than just a password to log in. Users continue to enter their regular username and password credentials to the dashboard login page, and then are required to enter a verification code which is sent to the user’s mobile phone via SMS. It’s secure, available at no charge for all Enterprise accounts, and setting it up is as easy as 1-2-3.
Using two-factor authentication ensures account security even in case someone writes down a password and leaves it visible to others. This is especially useful for larger organizations that have multiple network administrators.
Organization administrators can require two-factor authentication for their network administrators simply by checking a box in the organization settings page.
Users add their mobile phone number through the SMS setup page, found via the my profile page.
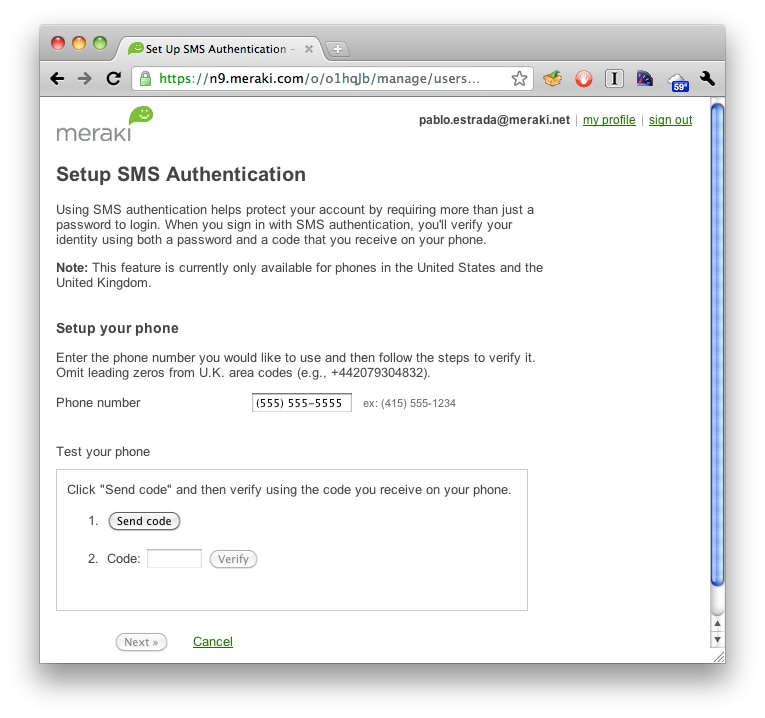
After enabling the two-factor authentication requirement, users logging in will be sent a verification code via text message, and will be required to enter it after entering their username and password credentials into the Meraki dashboard log in page. Logging in is straightforward:
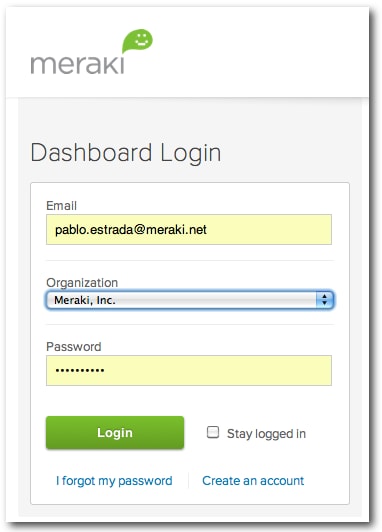
1. Enter Meraki dashboard username and password
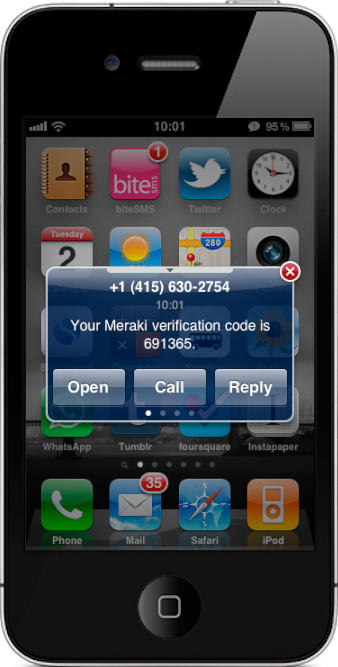
2. Receive SMS with verification code
3. Enter verification code into dashboard
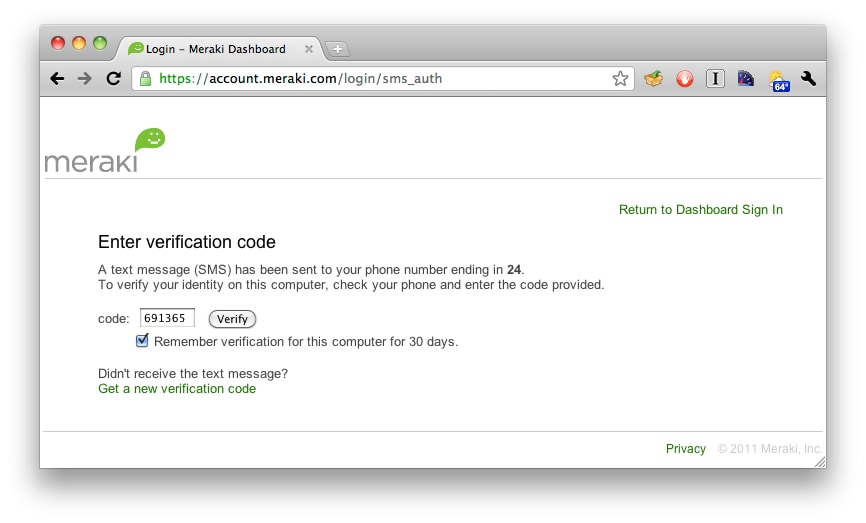
That’s it! This provides another layer of protection for the dashboard account. After entering the verification code the user is sent to the dashboard page for his or her network.
We’ve also added some more account security features, including password strengthening and re-use policies, and account timeouts and lockouts (see figure 1). More information about security and reliability information of Meraki’s cloud services can be found at meraki.com/trust.