We may not see it or feel it, but it’s happening. IoT devices are growing in number all around us, and improving our lives. Sensors help organizations streamline operations at a hospital, and point-of-sale devices improve our experience at the local coffee shop. But, securing IoT can be complicated, especially when contending with outdated devices, and deploying them across multiple sites. IoT devices typically lack 802.1X support and can be hacked in 5 minutes on average. In our recent “Security Made Simple” launch, we discussed a new feature called Identity PSK that simplifies IoT security.
A better way of securing IoT
Many IoT devices are not compatible with 802.1X, leaving IT admins no choice but to use WPA2 or a pre-shared key for authentication. Unfortunately, both methods come with well-documented security flaws. Identity PSK provides a way to assign users and devices unique keys, build identity-based groups, and scale them across the network. For example, a hospital might have wireless infusion pumps and patient monitoring tools for which they would like to apply different group policies. With IPSK, the hospital IT administrator can now assign those devices unique groups and separate VLANs. The IT admin will also be able to reset or change the keys on entire groups of devices at the same time.
With IPSK, it will become easier to secure devices across multiple industries. An IT admin at a manufacturing plant will segment barcode scanners and sensors into different groups. Retail point-of-sale devices and smart thermostats will connect to one SSID, yet have different security policies. On a college campus, gaming devices, RFID card readers, and printers are easily segmented when connecting to Wi-Fi. Hotels can onboard wireless users quickly and provide granular control over their access in a more simple and secure way.
Configuring Identity PSK
Identity PSK provides the simplicity of PSK with the benefits of 802.1X, and is available today in the Meraki dashboard. Configuration is located in the wireless access control section of the dashboard. The current implementation uses a RADIUS server for authentication, allowing organizations to leverage existing services such as Cisco ISE. When a client associates to a Meraki access point, the AP will send the MAC address of the device to the RADIUS server. The RADIUS server is able to respond with the PSK, which then allows the access point to authenticate the device.
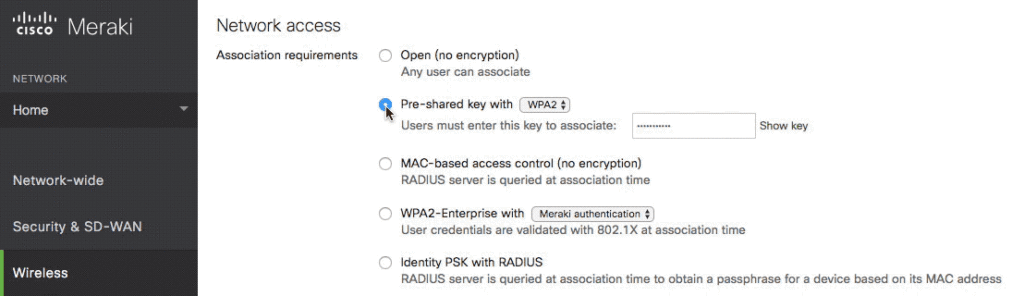
You can learn more here about how Meraki is simplifying security for every layer of the network, from client to application. For a further deep dive on Meraki Wireless, join us for an upcoming live webinar.